> things in different way, or maybe in some places it makes business
> sense to have these two separate functions I really don't know but at
> least semantically information risk also implies IT risk.
Not entirely: some IT risks (which some might take to mean "Risks affecting IT department" as well
as "Risks affecting IT") could be classed as general business/commercial risks, financial risks,
compliance risks, HR risks etc., and these may or may not be classed as information risks. There
are no hard and fast rules here.
> thing is, if
> we as risk managers are confused as to what is the difference between
> the two then how are we going to market our agenda to our clients, or
> educate people about the different types of risk?
True, and that's why it is so important for us to continue considering and discussing thorny topics
like this. I encourage anyone who is genuinely interested in furthering their knowledge to read
more widely than just the forum, valuable though it is. Google is your friend and Amazon is a pal.
By all means introduce concepts from other sources here but please reference them so that we can
read further when the need arises.
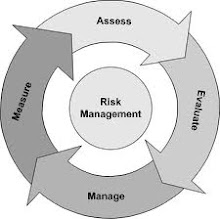
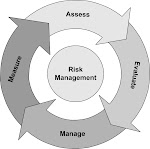
In that spirit, I'll quote two paragraphs from ISO/IEC 27005:
"A systematic approach to information security risk management is necessary to identify
organizational needs regarding information security requirements and to create an effective
information security management system (ISMS). This approach should be suitable for the
organization´s environment, and in particular should be aligned with overall enterprise risk
management. Security efforts should address risks in an effective and timely manner where and when
they are needed. Information security risk management should be an integral part of all information
security management activities and should be applied both to the implementation and the ongoing
operation of an ISMS.
Information security risk management should be a continual process. The process should establish the
context, assess the risks, treat the risks using a risk treatment plan to implement the
recommendations and decisions. Risk management analyses what can happen and what the possible
consequences can be, before deciding what should be done and when, to reduce the risk to an
acceptable level."
Kind regards,
Gary
Gary Hinson
Information can exist without the IT, hence it encompasses a broader
horizon, whereas IT is only a part of the information handling and
management process.
Take for example Risks involved in the internal employees behaviour
with respect of IS. It may or may not encompass the IT
infrastructure; or take the example of IS risks with outsourced
processes.
There are many such examples, which clearly shows the difference
between IS and IT risks.
Hope it clarifies.
Regards,
Surendro















.jpg)





.jpg)

.jpg)









.jpg)

.jpg)














.jpg)


.jpg)


























































































































































































































.jpg)

.jpg)











.jpg)




















































.jpg)
















.jpg)












































































































































.jpg)

























No comments:
Post a Comment