Our mission
OECD brings together the governments of countries committed to democracy and the market economy from around the world to:
- Support sustainable economic growth
- Boost employment
- Raise living standards
- Maintain financial stability
- Assist other countries' economic development
- Contribute to growth in world trade
The Organisation provides a setting where governments compare policy experiences, seek answers to common problems, identify good practice and coordinate domestic and international policies.
| Andrés Velasco, Finance Minister of Chile | Enlargement and enhanced engagement OECD also shares expertise and exchanges views with more than 100 other countries.
In May 2007, OECD countries agreed to invite Chile, Estonia, Israel, Russia and Slovenia to open discussions for membership of the Organisation and offered enhanced engagement to Brazil, China, India, Indonesia and South Africa. While enhanced engagement is distinct from accession to the OECD, it has the potential in the future to lead to membership.
| ||
Monitoring, analysing and forecasting
For more than 40 years, OECD has been one of the world's largest and most reliable sources of comparable statistics and economic and social data. As well as collecting data, OECD monitors trends, analyses and forecasts economic developments and researches social changes or evolving patterns in trade, environment, agriculture, technology, taxation and more.
Publishing
OECD is one of the world’s largest publishers in the fields of economics and public policy. OECD publications are a prime vehicle for disseminating the Organisation's intellectual output, both on paper and online.
Publications are available through OLIS for government officials, through SourceOECD for researchers and students in institutions subscribed to our online library, and through the OECD Online Bookshop for individuals who wish to browse titles free-of-charge.
Also available:
Related documents:
more
Challenging IS and ISM Standardization for Business Benefits - A business-practitioner’s viewpoints - Presentation Transcript
- Challenging IS and ISM Standardization for Business Benefits - A business-practitioner’s viewpoints Juhani Anttila Academician, International Academy for Quality (IAQ) Venture Knowledgist Quality Integration Helsinki, Finland juhani.anttila@telecon.fi , www.QualityIntegration.biz February 17, 2010 These pages are licensed under the Creative Commons 3.0 License 1 http://creativecommons.org/licenses/by/3.0 (Mention the origin)
- Challenging IS and ISM Standardization for Business Benefits Key themes: IS = Information security 1. General ISM standardization ISM = Information security 2. Guiding principles and basic terminology in ISM standards management 3. System approach in ISM standards 4. PDCA model in the standardization 5. Business integration in the use of ISM standards 6. Business realities and ISM standardization 7. Business leaders’ awareness and commitment 8. ISM performance and development 9. Epilogs Focus on the ISM standardization of ISO/IEC JTC1 SC 27 (IT security techniques) - ISO/IEC 27000 family of standards 2 xxxx/2.1.2010/jan
- International information security standardization is a part of the general standardization with its pros and cons All standardization aims at: General standardization consists of • Improved business performance and international (ISO, IEC and ITU), regional, confidence, and quality of products national and business branch standardization: (goods and services) * Standards are voluntary but may become • Decreased operational costs obligatory through reference to the standards in • Improved communication between people and organizations contracts, regulations, etc. and in company internal standardization * Cons of general standardization: * Standards may consider both product • There is uneven and unbalanced groups of characteristics and managerial, operational or voluntary people participating the technical issues * standardization work. * A consensus approach is the core of the • Management of the standardization is weak. standardization process * • Only communally interesting issues are accepted to the final standard texts mainly due to the consensus principle. Pros of general standardization: • Only trivial means to implement the standard • Broad acceptance and distribution of the texts clauses may be considered in the standards. • Extensive expertise in preparing and commenting • Handling of the issues in the standard text is the standards superficial. • Wide commitment and recognition • Standardization process is very slow. 3 • No restrictions for innovative implementation • Standard publications and participating in standardization are expensive. 3759/2.1.2010/jan
- ISO/IEC JTC1/SC27 Standardization committee ”IT security techniques” The committee works with generic methods and techniques for information security and its management. The title of the committee does not reflect the whole area of the work in the committee. There are five working groups (WG) in the committee: All the working areas of the committee are practical topics to be applied in organizations. However, many texts are rather complicated or theoretical and not easily adoptable into organizational business cases. Particularly difficult is to recognize the consistency in the committee’s standardization. 4 3685/9.1.2010/jan
- There is a serious need to a family planning for the whole standards structure of the committee Basic standards for ISM of the family include three standards, ISO/IEC 27000, ISO/IEC 27001, ISO/IEC 27002 that are the most recognized reference documents for professional information security management world-widely. These basic standards should be understood as a composite package. However, many users take them only as separate documents. Roles of the individual standards and the package entirety are difficult to recognize even by the experts and the ISO/IEC JTC 1 SC 27 committee members. In addition to the basic set of standards, there are many other standards in the family, including ISO/IEC 27003, ISO/IEC 27004, ISO/IEC 27005, ISO/IEC 27006:2007, ISO/IEC 27007 and ISO/IEC 27011, and numbered drafts now at least until the standard ISO/IEC 27059 and all together ISO/IEC JTC1/SC27 has under consideration more than one hundred different subject items. There are also other international standards not prepared by ISO/IEC JTC 1 SC 27 that are considered as parts of this same family of standards, e.g. ISO 27799 for information security management in health care. There is a serious need to a family planning for the whole standards structure of the committee in order to avoid confusion and failures in the use of the standards. The user should clearly understand the whole set of the standards series and the position and role of its individual 5 standards. 3760/9.1.2010/jan
- A chaotic standardization situation for business practitioners In addition to ISO/IEC 27000 standards, there are lots of other "competing" international standards and de-facto standards considering information security management. E.g. ISO/IEC 20000, ITIL, COBIT, Sarbanes-Oxley Act, Basel ll, FISMA, HIPAA, GLBA, NIST, etc. include also information security aspects. These references may have many same or similar elements but there is not necessarily consistency e.g. in terminology and structure of realization. ISO/IEC 27000 standards have complicated links with many other management standards issued by other standardization bodies. Information security management standardization cannot be isolated from these other management standards. Many different management standards are (or even must be) applied simultaneously in organizations. ISO/IEC 27000 family of standards follow the same methodology that has been used in the well-known and much used ISO 9000 standard series for the quality of management. However, the result is very questionable. There should be much closer relationship between ISO/IEC 27000 and ISO 9000 standardization. Naturally in organizational cases ISO 9000 should be applied in ISO/IEC 27000 applications because ISM should be understood as a part of good management, and also ISO 9000 applications should take into account information security issues. Integrated use of different management standards is under consideration among 6 standardization bodies but not yet achived any satisfactory results. 3761/9.1.2010/jan
- What are the basic guiding principles for the foundation of ISO/IEC 27000 standardization? There are not any clear guiding information security management (ISM) principles defined particularly for the ISO/IEC 27000 standardization as e.g. there are quality management principles (QMP) in the case of ISO 9000 standards. Guiding ISM principles or core ISM values and concepts are the foundation for a decisive ISM realization and standardization. They are beliefs and behaviors of business-integrated ISM found in high-performing organizations for integrating IS performance and operational requirements within a results-oriented business. ISO/IEC 27001 refers to OECD’s nine complementary principles for information security management and culture “The adoption of the PDCA (Plan-Do-Check-Act) model will also reflect the principles as set out in the OECD guidelines governing the security of information systems and networks.” This is referred only in ISO/IEC 27001 and is not valid for the whole ISO/IEC 27000 standards family, and otherwise OECD principles do not cover the whole scope of ISO/IEC 27000 standards. Factually the whole referred sentence is absurd because correlation between PDCA model and OECD principles is at least unclear. Without a consistent foundation of guiding principles of the ISO/IEC 27000 family have very obviously developed on the basis of individual, spontaneous and inconsistent initiatives. 7 3762/9.1.2010/jan
- ISO 9000 quality management principles, QMP These principles can be used by senior management as a framework to guide their organizations towards improved performance. The principles are derived from the collective experience and knowledge of the international experts: * Principle 1: Customer focus * Principle 2: Leadership * Principle 3: Involvement of people * Principle 4: Process approach * Principle 5: System approach to management * Principle 6: Continual improvement * Principle 7: Factual approach to decision making * Principle 8: Mutually beneficial supplier relationships Factually these are principles for a good organizational management. They are relevant for: all areas an organization’s business management all expert disciplines wihin business management, 8 including information security 3746/12.1.2010/jan
- Basic terms and definitions are not considered consistently or logically in the ISO/IEC 27000 standards. • Definition of information security: “Preservation of confidentiality, integrity and availability of information, and ... other properties can also be involved” This not any proper definition. It is only an open list of issues. The definition is reactive, not covering proactive aspects. The definition should be consistent with the concepts of information, knowledge and security. Basic dimensions characterizing information security in its “definition”, integrity, availability and confidentiality, are very difficult concepts to understand by business people. Even experts have different opinions about these concepts. • The key concept information security management (ISM) has not been defined at all in the ISM standards. • Privacy is a very central and significant concept in the ISM standards. Its role is vague in the standards. • The definition of information security assurance (ISA) and its relationship with ISM are unclear in the standards. • ISO/IEC JTC1/SC27 has also started to consider the governance. This is causing confusion among standards users because the relationships among the key managerial concepts are clear: (Organizational) business management, corporate governance, IT governance (ITG), ISM, information security governance (ISG), and ISA. These are used in many documents. Business people should be able to deal with the concepts consistently and effectively in practice. 9 • There is no systematic concept analysis in the ISM standards as used e.g. in the standard ISO 9000. 3765/12.1.2010/jan
- Defining the concept information security management For time being, one of the most central concepts, ”Information security management”, has not been defined at all in the ISO/IEC 27000 standards family. The definition may be, however, created by the reference to the standardized definitions of other analogical concepts, e.g. quality management and risk management: Information security management: Coordinated activities to direct and control an organization with regard to information security Note: Information security management is not management of information security but management of an organization. This means an integrated information security management: Information securuty management is a responsibility of the business management, and it is taking place through the managing actions of business leaders. Experts have assisting roles both in information security management. 10 3763/3.1.2010/jan
- ISO 9000 Quality management principle #5: System approach to management ”Identifying, understanding and managing interrelated processes as a system contributes to the organization's effectiveness and efficiency in achieving its objectives” Key benefits: • Integration and alignment of the processes that will best achieve the desired results. • Ability to focus effort on the key processes. • Providing confidence to interested parties as to the consistency, effectiveness and efficiency of the organization. Applying the principle of system approach to management typically leads to: • Structuring a system to achieve the organization's objectives in the most effective and efficient way. • Understanding the interdependencies between the processes of the system. • Structured approaches that harmonize and integrate processes. • Providing a better understanding of the roles and responsibilities necessary for achieving common objectives and thereby reducing cross-functional barriers. • Understanding organizational capabilities and establishing resource constraints prior to action. • Targeting and defining how specific activities within a system should operate. • Continually improving the system through measurement and evaluation. 11 This principle is relevant for all areas of organizational management. 3728/2.1.2010/jan An organization is managed as one single system.
- Information security management system (ISMS), a core concept in information security standardization There are two elements in the concept information security management system, ISMS: 1. Management System (of an organization), MS: - System to establish policy and objectives (of an organization) and to achieve those objectives 2. Information security, IS: - A qualifier (attribute) characterizing a management system (MS) characterizing how IS is taken into account in the management system ISMS = = IS of/in/for MS ISMS =/= System for information security ISMS is a concept for systematic approach, “systematicity”, for IS in an organization’s management. ISMS is principally aimed for organization’s own internal business management needs and purposes. In fact, the concept ISMS is not at all needed for practical management approaches in organizations. It has caused a lot of confusions, especially when translated into 12 different languages. 3764/2.1.2010/jan
- Information security management (ISM) and information security assurance (ISA) - Difference and consistency There are two different but consistent viewpoints to managing information security in an organization: A. Information security management (ISM) for organizations’ internal management needs B. Information security assurance (ISA) that aims to create and strenghten confidence among an organizations’ external stakeholders. ISA is chiefly a communication issue. ISA is a part of ISM! ISO/IEC 27000 standards do not make clear linkages between ISA and ISM. For this standards ISO/IEC 27001 and ISO/IEC 27002 have the most essential role. Now their relative positions are not clear. A natural possibility is to apply the same approach as in ISO 9000 standards series with the standards ISO 9001 and ISO 9004: ISO/IEC 27002 is for ISM (Guidance) ISO/IEC 27001 is for ISA (Requirements) ISO/IEC 27002 should never be understood as a guidance for ISO/IEC 27001 clauses. Standards should be applied creatively in the both domains of ISM and ISA. 13 3767/13.1.2010/jan
- Two principal domains, management and assurance, of the organizational management AA/B Organization A MA AB/C Organization B1 MB1 Organization C Aim of the approaches: Organization B2 M Excellence (internal interest) MC A Confidence (external interest) MB2 Management disciplines: - MA, MB, MC:O rganization-internal (business) management (system) - AA/B, AB/C: Assurance between organizations (based on organization-internal management system) At all organizational levels there should be consistency among these disciplines. Both management 14 and assurance consist of many different expertises. 3733/3.1.2010/jan
- Information security management and assurance as consistent parts in an organization’s management ISM business system aspects ISM = Information security management (focus on excellence of a business approach), ISO/IEC 27002 ISA = Information security assurance (focus on confidence for Tailoring case-by-case conformity in an organization’s product provision), ISO/IEC 27001 ISA elements ISM covers the whole business management system (BMS). ISM principles 15 3653/15.1.2010/jan
- System concept System (*) is a set of interrelated or interacting A system’s Management elements (processes). creators and owners - A system is an entity that maintains its existence and functions as a whole through the interaction of its parts. A system - A system has always an aim or purpose defined (and its elements) by the system’s creators or owners. The system is just created to accomplish its aim. - A system has interactions and transactions with its environment to get input from and to provide Inputs and outputs through output for system’s stakeholders. Stakeholders interactions and transactions may set requirements to the system. - A system is managed as a whole. Management is System environment based on knowledge and information and PDCA (Stakeholders and system-competitors) management model (feedback). An organization is a system. System management domain System requirements Internal interest External interest 16 Effectiveness and efficiency Effectiveness (Ref. Russell's paradox) 3732/20.1.2010/jan (*) Ref. ISO 9000 definition
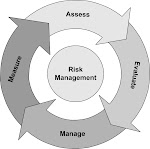
- The PDCA (Plan-Do-Check-Act) is a recognized multipurpose model for business management. The PDCA Model (called also as Deming / Shewhart Cycle) has a long history and a great variety of different applications, possibilities, and uses in the field of general business management: – Original PDSA (Plan-Do-Study-Act) model was created by American Walter Shewhart in the 1920’s and used for production control. – The model became popular through American W. Edwards Deming’s lectures of managerial quality during several decades (from 1950’s to 1990’s). – American Joseph Juran’s Trilogy Model (1964) contains the same elements as the PDCA model. He especially emphasized differences between control and breakthrough. His spiral model was presented in his well-known Quality Control Handbook (1975). – In the 1980’s Japanese Kaoru Ishikawa and Masaaki Imai emphasized problem solving and continual improvement (“Kaizen”) according to the PDCA model. – Later Japanese Shoji Shiba has made remarkable work by combining the original PDCA model with the ideas of managing knowledge and of Buddhist philosophy. – In late 1990’s and early 2000’s the SixSigma methodology for large scale business performance improvements was developed by Motorola and became popular by its successful application in General Electric. Also SixSigma is based on the PDCA approach. – The PDCA model has also consistent linkages with traditional systems theory and systems dynamics. – To the international standardization the model was used at first in standards ISO 9000:2000 for 17 quality management from where it came e.g. to information security management standards a few years later. However, it is used very superficially in standardization. 3119/2.1.2010/jan
- A triple PDCA (*), a model for good management: Coordinated activities to direct and control an organization (**) ACTING (A): PLANNING (P): • Preventing actions • Business and • Improving actions management models • Re-engineering • Business plan Applying a triple PDCA model • Communicating • Approaches and (“The Eyes of Buddha” (***)): • Recognizing and methodology 1. Rational control (operational) rewarding A P 2. Continual rational small step C D improvement (operational), CHECKING (C): DOING (D): “Kaizen” approach • Assessing the • Deploying the approach 3. Innovative breakthrough performance and achieving the results changes (strategic) • Reviewing the • Controlling operational performance performance • Corrective actions 18 2343x/15.12.2008/jan (*) Deming / Shewhart, (**) ISO 9000, (***) Shiba; Bodhnath Stupa, Kathmandu
- Information security management: Planning, controlling, and improving the performance of business processes Performance (5) New performance A P planning Good C D Control with the new limit A P (4) Breakthrough C D improvement (2) Performance control (3) Small step improvement ”Kaizen” (1) Performance A P planning Control limit Prevention C D Bad Rectifying sporadic problems Time 19 Feedback 3766/12.1.2010/jan (Ref. Dr. Juran: Trilogy Approach)
- Integration is the main strategy for a professional expertise approach within an organization (system) Integration means: Expertises may include: • Implementing effective and efficient expertise –Finance items embedded within normal business –Quality management activities (especially in business processes) –Business risks • Acting against building distinct ”expertise –Information security systems” (i.e. lack of integration). Business- –Human resources separated expertise initiatives are artificial. –Information and communications –Knowledge One must understand and take into account the –Occupational health and safety nature of the organizational system, its business –Environmental protection and its realities when implementing expertise –Innovation initiatives of business management. Integration is always an organization-dedicated solution. –Ethics –Social responsibility Cross-application of all expertise areas is needed. –etc. E.g. information security is needed in quality management and quality in information security 20 management. 3745/2.1.2010/jan
- Business-integration of the standards ”systematicity” Business standards are established through orgnizations’ internal business structures and processes. A separate management system is artificial. 21 Systematicity means illusion. 3704/7.1.2010/jan
- Management integration takes place at two levels • The strategic level, where one makes decisions and undertakes measures concerning the entire organization (business system of business processes) and considers especially the future competitiveness of the organization. • The operational level, where decisions and measures concerning daily management are made and undertaken. Emphasis is on operational questions of the individual business processes. These two managerial areas are very different by their purpose and therefore different methodology is needed for them. Integration covers all aspects needed for the management of an organization. 22 3731/23.8.2009/jan
- Necessary emphases in modern X management? 1. Integration: – Implementing effective / efficient and business- X management relevant X principles and methodology X of/in/for management embedded within organization’s normal activities of strategic and operational management 2. Responsiveness: – Being able to adjust quickly to suddenly altered Dynamic and flexible external conditions, and to resume stable business management operation without undue delay 3. Innovation: Standard approach – Striving continuously for new organization- dedicated innovative and unique solutions and An organization’s unique encouraging various choices for X management approach in different organizations. 23 3737/2.1.2010/jan
- Integrating specialized domains of management standardization and ensuring natural business diversity The Finnish model Finance for integration (MSS) Product General management Environment quality system based on PDCA General Occupational management Ethics responsibilities health and safety and business Organizational system identity & privacy Social Security responsibility Risks Organizational diversity 24 3342/20.8..2009/jan (Ref.: ISO Management systems standardization, MSS)
- From a business establishment Promotion and support: to satisfying AN ORGANIZATION * Standardization * Political impact requirements * Consultancy * etc. Business activities: -Operational duties- -Strategic development- Action plans Infrastructure Management + Management system Owner, Strategies Vision Mission Values and Policies Stakeholders + Needs and expectations: * Performance Competitors (Business creator) apprecia- * Price and cost + tions Purpose 25 Profound knowledge: Business management sciences and experiences + Expertises in quality, information security, environmental protection, etc. 3749/25.1.2010.2009/jan
- Standardization and users’ business reality Standardization Y: Issue Y / Standard element Y / Consensus process Y Standardization X: Issue X / Standard element X / Consensus process X Standardization subject area Practical realization of the subject area Organization A: Realization elements A: Innovation process A 26 Organization B: Realization elements B: Innovation process B 3516/27.8.2008/jan
- Organizational information security originates in business processes. All business results are achieved through managing business processes. Processes adhere to all kinds of daily doings or activities within any organization. In integrating information security in organizations, it is important to understand information security issues in the context of business processes. All business process activities are very strongly information-intensive, and information flows between these activities and between different performers and even between distant operational locations. Information security is affected directly in real time through process arrangements, tools, technical systems, and people in practical work and how these are managed by appropriate and systematic practices. However, truly effective and efficient process management implies a radical change to the established management thinking and structures in many organizations. This should be taken into account in information security management realizations, too. Although the standards explicitly refers to the process approach, however, it is applied in the standards unsystematically, inexplicitly, and poorly that does not support effectively established business practices. E.g. ISO/IEC 27002 says: “The process approach ... presented in the ISMS family of standards is based on ... the PDCA process.” This sentence is completely nonsense! 27 3770/12.1.2010/jan
- ISO 9000 Quality management principle #4: Process approach ”A desired result is achieved more efficiently when activities and related resources are managed as a process.” Key benefits: * Lower costs and shorter cycle times through effective use of resources. * Improved, consistent and predictable results. * Focused and prioritized improvement opportunities. Applying the principle of process approach typically leads to: * Systematically defining the activities necessary to obtain a desired result. * Establishing clear responsibility and accountability for managing key activities. * Analysing and measuring of the capability of key activities. * Identifying the interfaces of key activities within and between the functions of the organization. * Focusing on the factors such as resources, methods, and materials that will improve key activities of the organization. * Evaluating risks, consequences and impacts of activities on customers, suppliers and other interested parties. 28 This principle is relevant for all areas of organizational management. 3738/2.1.2010/jan An organization is managed as one single system of processes.
- Historical notes for the process approach • Process approach was used already in ancient plant and construction activities. The concept is often referred to in cases of natural development. • Through industrialization processes became an everyday concept in so called process industry. • From 1980’s process approach has been used for computers’ internal activities according to structured analysis and design technique (SADT). • In a large scale business process approach has been used comprehensively for the benefits of business management only for less than twenty years, and during that time a lot of practical means have been developed for that purpose. • Process management thinking got learning from system theory and system dynamics. • To the quality management standards ISO 9000, process concept was introduced in the 1990’s and just in very recent years the methodology came to the other international management standards, e.g. information security management standards. • BPR (Business Process Reengineering) is a concept for process improvements according to the ideas of PDCA model. It was particularly promoted by Michael Hammer, James A. Champy and Tom Peters in the 1990’s. • BPM (Business Process Management) has become during the recent years a popular concept within IT experts in automating business processes according to SOA (Service Oriented Architecture) principles. • Today organizations’ all business processes are “complex responsive processes of relating”. 29 3122/20.3.2009/jan
- What is a (business) process? Process means a continuous(*) activity by organized resources for fulfilling organization’s basic duties: – Processes put into practice organization’s business / action plan. – Operational every day work is done in processes. Process – Processes produce outputs (results) to the stakeholders. (acting) There are always processes in all organizations. Structure (e.g. organizational structure) is a contradictory dimension to the processes. The both are needed – in fact they are also always existing in organizations. They cannot be replaced by each other. Process is the primary one, The structure Structure should serve it. (existing) Modern organizational processes are “complex responsive processes of relating”. The key business management from the quality point of view is: How to manage business processes? 30 3041/20.8.2005/jan (*) A project is a singular or unique process.
- The process/structure dilemma: Managing for balance Functionality Structure #1 Structure #2 Process (doing, acting): Real time Active Balance issues: Skilled - Freedom / control Emergent Agile - Awareness / instructions Adaptive - People / systems Flexible - Proactive /reactive Open Free Living Structure- stiffness Structure (being, existing): Planned, Built, Passive, Past, Prescribed, Stagnant 31 3723x/3.11.2009/jan
- A P A comprehensive process management model C D Business performance assessment and review Process performance assessments (audits) Re-design and Corrective Conformity re-engineering action check M Performance control e a Business outcomes A business process Output s Process Inputs data u • require- outputs Work activity r ments Internal • needs data e Other • requisites Other m processes People resources Procedures e n t 32 Other processes Preventive action, improvement Analysis 0588/28.3.2004/jan
- New foundations for business infrastructure Uncertainty and ambiguity Emergence and self-organizing networks of actors Many heterigeneous global actors in virtual networks All linked with everything else, all linkages not known Customers and other stakeholders differentiating with singular needs Pradoxal freedom of the actors (”both-and” instead of ”either-or”) Signifigance of immaterial issues (information, knowledge, services) Informal learning and serendipity Increased speed of activities and change Signifigance of transaction phenomena Complex responsive processes of relating Simultaneous agility and maturity requirements Immense pressure / stress of business leaders Certainty and predictability 33 1544/2.9.2009/jan (Refs.:D Zohar, R D Stacey)
- Problem and challenge of the information security profession to adapt to the needs of modern society Changed business environments cannot be avoided: “No boundaries – The old boundaries have been obliterated. Today’s trends increase uncertainty, variety, variability, dynamics in all areas of business management.” Marshall McLuhan: ” Today each of us lives hundred years in a decade.” Speed Business Changes environments Agility and society Complexity Problem, ”crisis of information Diversity security management” Immaterialness Variety Information Preferred scenario: security - Global adaptation: Evolution profession in toward a synergistic society its entirety - Breaktrough transformations 34 needed in the information Time security profession 3641/12.1.2010/jan
- Activities within complex responsive processes of relating All kinds of activities Low Innovation may exist in networking Chaos Creativity processes. Anarchy Political Debate Agreement control - “Zone of compromise Complexity” Serendipity Trial & Error Standards Guidance Experimenting High Monitoring High Certainty Low 35 3430/15.1.2008/jan (Ref.: Stacey: http://www.plexusinstitute.org/edgeware/archive/think/main_aides3.htm l)
- Information security management is based on organizational information / knowledge Operational procedure documents, standards, operation records, factual knowledge, etc. (explicit contents) Conscious Reality of the management in the minds of the individuals and in the practical operations Sub- (implicit / tacit contents) conscious – This part is the most significant regarding to the actions for the management realization. – The contents may change due to time and situation and depending on influences and learning. 36 3758/9.1.2010/jan
- Empirical fact-based information and inherent knowledge are needed for successful management Wisdom - myths - values Knowledge Intervention - explicit records Reflecting and deciding - tacit knowledge Plan / Act (know-how, competence) Information ”Ba” Analysing You get what A P you measure Data C D Environments Measuring ... Facts Effects 37 The performance reality of the company business processes 0609/25.3.2008/jan
- Business people are not adequately committed to information security management Studies and observations made in small and big companies and governmental offices: Although: • Most people in our organizations know the fundamentals and basic principles of IS and recognize their importance, and even may be well-motivated. • There is a lot of general and organization-dedicated IS training and education programs for increasing awareness and skills of IS. However: • Senior executives in those organizations: – Are not really interested in information security in their own management practices – Don’t understand or recognize their managing role for information security – Have only a superficial understanding of information security – Lack the necessary skills for managing an organization with regard to information security – Senior executives are not familiar with the information security standards – Easily delegate their responsible duties to external consultants or even outsource the whole issue 38 3183/22.1.2010/jan
- Why business leaders are poorly commitment to information security management? • Basic professional IS concepts, e.g. integrity, availability and confidentiality, are difficult, complicated and strange to business people. • Information security management requires specific knowledge and skills. • Guidance materials for information security management are complicated and confusing, and difficult to realize and apply consistently: – General standards and guidelines, e.g. ISO/IEC 27000 family of standards and OECD Guidelines – Information technology and service references that normally consider also information security aspects, e.g. ISO/IEC 20000, ITIL, COBIT, Sarbanes-Oxley Act, etc. • General management references, e.g. ISO 9000 standards, extensive and multifaceted general management literature, and management education, e.g. MBA programmes, don’t clarify information security as a management issue and don’t explicitly promote the issue. • Information security is a multidisciplinary issue and difficult to cope with simple managerial practices - and particularly in today’s turbulent business environments. • Communication between business leaders and information security (and other related) experts is ineffective and uncreative in general and within organizations. • Business leaders are very busy, subjective, authoritative, and holistic generalists. • External third party audits and certifications undermine business leaders’ active responsibility. • Business information is principally based on tacit (implicit) knowledge, and management of 39 the security of tacit knowledge is a sophisticated issue. 3186/22.1.2010/jan
- Consequences when senior executives don’t commit to information security management • Information security is not being managed business-minded and not aligned with real business needs. • Information security is seen only as a reactive and negative question to fulfil some standardized requirements. • Organizations keep busy with separate and restricted information security questions • Information security standards are not understood from the managerial responsibility • Organizations take only “cosmetic” or superficial actions for information security management. • Business leaders delegate their management responsibilities to experts or outsource the whole issue to external consulting organizations. • Organizations keep silent on their problems or incompetence in information security – and suffer consequences, or hope that nothing serious will happen. 40 3187/22.1.2010/jan
- Information security management performance is not any ON / OFF issue! YES (1) Information security performance NO (0) NO YES Specific actions (measures or tricks) 41 3757/3.1.2010/jan
- An organization’s business performance (from early stage to maturity) – Information security integration All business performances (including information security) are fuzzy issues: Excellence 1 = perfect Grade of business performance Leadership Organizations with a third party Competitive- certificate (*) ness Need of change? How to get the change happen? Effectiveness Beginnings 0 = good-for- Anecdotal nothing 0 10 30 40 60 70 90 100 Assessed overall business performance % (*) Third party certifications do not define any particular level of performance. Organizations cannot differ from the others on the basis of third party certificates 42 2460/2.1.2010/jan
- Epilog 1: Situation and challenge There are significant inadequacies, inconsistencies and other problems in the general international standardization and standards mainly due to the normal standardization processes. Individual organizations applying the general standards should highlight their own responsibility of business leaders and experts in order to achieve the benefits. A continuously increasing awareness and knowledge, innovations, and courage would have required to create and implement useful and organization-dedicated solutions when applying the standards in real business environments. There should also be an effective cooperation of business leaders and information security experts. A proactive standards recognition may be promoted by active participation in standards preparation and commenting. 43 3772/12.1.2010/jan
- Theses of the new approach for applying information security management standards Striving for a competitive information security integration by: • Recognizing performance excellence instead of a narrow information security conformity thinking • Striving for a systematic approach (“systematicity”) of the information security in management instead of formal and distinct information security management systems • Using business-related information security management principles and actions instead of fulfilling formal and general information security assurance requirements only • Aiming at innovative and unique solutions instead of stereotyped systems • Relying on internal business performance self-assessments and advanced information security assurance communication instead of third party audits and certifications of “artificial” information security management systems • Getting advantage of tacit knowledge instead of only records of explicit data and information • Networking with partners and recognized world-wide communities of multifarious expertise • Supporting various ways of collaborative learning instead of narrow-minded and reactive control only • Reinforcing and using company’s own internal awareness and expertise instead of passive use of external consultants 44 3768/12.1.2010/jan
- Epilog 2: Keep your organization’s identity in applying general information security standards There will be also in future standards-experts who don’t understand or don’t want to understand business realities of real organizations. Consensus process of standardization has a detrimental influence on the clarity and ambiguity of general standards: “Stupidity condenses in the masses - The mob has many heads but no brains” However, standards must not hinder creative applications of the standards by responsible organizations. 45 3769/12.1.2010/jan
- Juhani Anttila, Independent Expert Independent expert, Venture Knowledgist • Expertise of more than 40 years in the field of quality and 20 years of information security • 35 years at different quality related positions at Telecom Finland and Sonera Corporation • Several decades’ involvement with international and national standardization of quality, reliability, information security and telecommunications • Many years Assembly Representative and Vice President of the European Organization for Quality (EOQ) • A founder and developer of the Finnish National Quality Award, Developer and assessor of the European Quality Award • International Academician for Quality (Member of the International Academy for Quality) • Honorary Member of the Finnish Society for Quality, Honorary Fellow Member of Quality and Productivity Society of Pakistan • Board member or chairman in some companies • Expert adviser in several organizations in quality management, dependability management, information security management, crisis management and social media, and lecturer in some universities • Expert in projects in some developing countries • Contributing by writings, lectures, and speeches globally on five continents 46 3678x/3.5.2009/jan (Ref.: http://www.qualityintegration.biz/contacts.html )
202 views, 1 favs, more stats
More info about this presentation
© All Rights Reserved
Go to text version
- Total Views 202
- 201 on SlideShare
- Comments 0
- Favorites 1
- Downloads 25
- Upload Info
- Uploaded via SlideShare
- Uploaded as Adobe PDF
Categories
ISMS pptation
go here































.jpg)





.jpg)

.jpg)









.jpg)

.jpg)














.jpg)


.jpg)


























































































































































































































.jpg)

.jpg)











.jpg)




















































.jpg)
















.jpg)












































































































































.jpg)

























No comments:
Post a Comment