Friday, October 17, 2008
How to develop and maintain the ISMS
Implementing an ISMS — LRQA Guidance
1. Overview2. Introduction to Implementing an ISMS3. The OECD Guidelines4. Getting started5. Planning for success6. Understanding the standard
7. Where next...?8. Management processes9. Define the scope10. ISMS policy11. Risk assessment and management12. Risk treatment13. Certification
Implementing an Information Security Management System (ISMS) — LRQA Guidance
Why is BS7799 (ISO 17799) good for you?
Whether you manage internal information management systems, are responsible for information security or develop IT products and services for your customers, effective information security management systems (ISMS) are essential. They will help ensure you develop the right controls, systems and products to meet the ever increasing and demanding requirements of your customers and partners.
BS7799 aims to ensure that adequate controls (addressing confidentiality, integrity and availability of information) are in place to safeguard the information of ‘interested parties’. These include your customers, employees, trading partners and the needs of society in general.
An ISMS compliant to BS7799 part 2 can help you demonstrate to trading partners and customers alike that you take information security seriously. Accredited certification to BS 7799 is a powerful demonstration of an organisation’s commitment in managing information security.
This article provides some practical guidance and advice for those who have been tasked in gaining certification for their organisations with regards ISMS. A complementary document: ‘Implementing an ISMS - a Consultant’s Viewpoint’ is currently in preparation.
This article has been written by Geoff Brooks, LRQA Technical Services Manager
more
Implementing an ISMS — Consultants Viewpoint
1. Overview2. Benefits3. The initial steps4. Selecting a consultant5. Scoping the system6. Deriving the list of assets
7. Risk assessment8. Statement of applicability (SoA)9. Audit the system10. Certification11. Sources of further information
Implementing an Information Security Management System (ISMS) — Consultants Viewpoint
Is ISO 27001 right for your organisation?
In today's information society, electronic data is critical for almost everything we do. We rely on Internet connectivity and email. Laptops and PDA's have enabled a new mobile workforce. In short, information has now become a truly business critical asset. Protecting this asset through developing robust information security strategies and implementing effective information security controls is a key management responsibility.
Additionally, on account of the ever-increasing amount of legislation relating to the processing and storage of information, managers have a statutory responsibility to ensure that their company's data is protected.
Most companies will have implemented an information security management system to one degree or another. Achieving full compliance with a recognised industry standard is a way of demonstrating to clients, both existing and potential, as well as to shareholders, that your company is serious about information security governance.
ISO 27001 is the international standard for information security management and provides the ideal benchmark for certification. The benefits of embedding this standard in your information security management system (ISMS) should become apparent in the very early stages of implementation - and deliver lasting value to your organisation.
The purpose of this article is to help managers decide if a formal ISMS is appropriate for their organisation. It is written by Malcolm Armitage, a registered CISSP (Certified Information Systems Security Professional) with (ISC)².
Malcolm is a Director with SeQuality Management Solutions Ltd (www.sequality.co.uk) with many years experience helping organisations develop and implement such systems and achieve ISO 27001 certification. It is written from the consultant perspective and is designed to be read in conjunction with the LRQA Guidance article.
This article has been written by Malcolm Armitage, Independent Consultant.
First Previous Next Last
Benefits
Clients have cited several benefits associated with implementing a formal ISMS and achieving certification:
Increases potential client base and sales pipeline through satisfying specific contractual demands
Protects the value of IT investments
Reduces reputational risk
Integrates disaster recovery / business continuity
Formalises the asset inventory
Avoids security incidents lying dormant and dropping off the radar
Embeds continuous improvement in information security processes
Assists external financial auditors and simplifies the audit process
First Previous Next Last
The initial steps
Let us look first at what we are trying to achieve by implementing an ISMS. In this day and age we rely more and more on information in electronic form (although paper documents must not be precluded from this). You should stand back and imagine how your organisation would (or could) cope if this key information was lost or corrupted, or its confidentiality was compromised.
A small company who may use a computer for payroll and a few letters would probably be not significantly disrupted if all were lost. Providing the payroll could be manually re-created and not too many key addresses were lost, business could continue as usual.
However, if a larger organisation suffered a similar incident just one of the following could be disastrous:
If the information became unavailable – imagine trying to access files or databases and they weren’t there and could not be reconstructed; or
if the confidentiality of the data was compromised and key addresses and personal information was available to unauthorised persons; or
if the data became corrupted – such as account details or the contact database.
An organisation could go out of business overnight if adequate steps had not been taken. So this is the starting point: – deciding if an ISMS is necessary. A full business case containing both financial and qualitative benefits should be developed.
With ISO 27001 the organisation has the option to ‘ring fence’ different activities. As an example, an organisation may decide to apply certain controls to specific contracts or certain processes.
It is essential to get top-level management buy-in, not just to authorise the expenditure but to covey to the organisation that information security is taken very seriously and that if policies aren’t adhered to, disciplinary action may be taken. A full business case containing both financial and qualitative benefits should be developed and this can help get senior management buy-in.
Once again, the initiative will fail without a high degree of management commitment.
A project team should be established with members from key departments – this should be a business initiative and not purely reliant on the IT department. This is to ensure that all relevant and applicable information is captured from around the organisation.
First Previous Next Last
Selecting a consultant
You may decide not to involve a consultant and go it alone, after all information security isn’t rocket science, just good business practice. You may choose a combination of both internal and external resource. However, it is important to factor in the cost of these internal resources into the business case.
Whichever way you look at it, there is a cost involved whether it’s fees paid to an external consultant or hours charged to the project by using internal resource. Don’t forget that the external consultants will have done this before and should be able to reduce the duration of the project.
When it comes to selecting an external consultant a referral must be the preferred option. One who comes highly recommended from a colleague or business associate knows that you are aware of his approach and method of working.
If a referral is not possible, consider contacting your local Business Link, (http://www.businesslink.gov.uk/) who have access to a national register of approved consultants. The assessment is independent and reviewed annually. The British Computer Society (www.bcs.org) also maintains a register of consultants known as The Professional Advice Register.
Another option is to approach the assessment companies. These often have a list of consultants that their clients have used. They may be able to supply a list of two or three people for you to consider.
There are many factors to consider when choosing a consultant which include:
Do they have recognised skills and qualifications which can be verified? There are several schemes that require consultants to take exams to demonstrate a level of competence and in some cases require CPD credits e.g.
(ISC)² - International Information Systems Security Certification Consortium administers the examinations for the Certified Information Systems Security Professional (CISSP). They provide a portal where a consultant’s qualification can be verified. http://www.isc2.org/
BCS – British Computer Society administers the ISEB (Information Systems Examinations Board) CiISMP exam. http://www.bcs.org/
Can they provide client references of successful implementations/certifications? It is important that you understand the past experience of the specific consultants that will be working on your project rather than simply the consulting company they work for. Most companies will be able to provide a page of logos – try to ascertain what was really achieved.
Do they demonstrate an understanding of your business and specific requirements? Consultants should recognise that every business is different and not simply attempt to roll out what they have done on previous projects. Their approach and experience should be tailored to your needs, rather than them tailoring your needs to their experience and methodologies.
If all the above factors are met, you should ask yourself the most important question: Do I like these guys? You don’t have to invite them to your house for dinner, but for the implementation to be successful you will have to develop a deep working relationship. Remember that, from your perspective, consultancy companies are only as good as the resources they put on the ground.
First Previous Next Last
Scoping the system
Consider carefully what the ISMS is intended to cover and what you expect to get from it. It’s important to include all the activities that fall within the scope of the ISMS. Should you seek formal certification, this is what your assessment body will use as the starting point.
Potential customers may well ask to see the approved scope to ensure you can provide, and are assessed to provide, exactly what they require.
The objectives should also be considered and documented. Think carefully about these. The days of ‘we want to be best in class’ have gone. The standards now require that an element of continual improvement is demonstrable.
Identify and engage key stakeholders and assemble the correct project team. Implementing an ISMS involves more than just the IT organisation and it is important that the business as a whole sees the benefits of the implementation and understands its impact. Team size and the appropriate project leader are specific to each organisation. The project team should be able to devote sufficient time to the implementation. A smaller group of closely involved individuals is usually more effective than a larger team of occasional part-timers. Should you have engaged a consultant, it is important that they are supported by internal resources: nobody understands the business better than those working in it. When consultants leave, knowledge can walk out the door with them.
As with any new project, a plan should be produced, but be realistic. If funding is sought from your local Business Link, they may require sight of the plan. The complexity of this will depend on the size of the organisation and the scope of the ISMS. You may decide that the ISMS is to be applied to only some activities within the organisation.
Try to keep your plan relatively simple yet include sufficient detail to show important milestones. Include review activities on the plan so that progress can be formally monitored. Update the plan on a regular basis. Ensure you keep senior management informed of progress.
First Previous Next Last
Deriving the list of assets
It’s important to establish just what needs protection. It may sound obvious, but the first part of understanding what you need to protect is understanding what you have. This is not always immediately apparent as it is important to value each asset not just in terms of financial value but also in terms of the impact such a loss would have on the organisation. In order to do this you should nominate representatives from each department or key areas. When building this list it’s important to capture all the obvious and important assets such as the electronic ones, but don’t forget the old analogue modem that’s used daily by accounts to pay people etc. Conversely, make sure that the not so important assets in the organisation are excluded.
Remember that you are trying to capture the key components that need consideration in terms of information security. Consider the ‘what if’ scenario on the selected asset: what would it mean in terms of financial loss or reputation if they became unavailable or corrupted (the business impact analysis). Also take into consideration the fact that company assets may be located offsite – laptops are an example of this.
First Previous Next Last
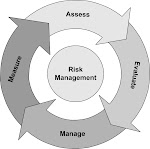
Risk assessment
Once the list of assets has been established a risk assessment methodology should be selected and undertaken on these assets. There are tools available to assist with the risk assessment process that may be worth considering. Which ever risk assessment methodology is selected it’s important that it is appropriate and repeatable.
A risk treatment plan should be produced to manage and mitigate the identified risks. Appropriate controls can then be selected from ISO 27001 Annex A to satisfy the risk assessment and risk treatment requirements.
First Previous Next Last
Statement of applicability (SoA)
An SoA must be prepared that shows the controls that have been selected from ISO 27001 and the reasons for their selection. It must also show the controls currently implemented. Where any controls have not been selected because they are inappropriate for the organisation, the justification for their exclusion must also be noted.
First Previous Next Last
Audit the system
As with other management systems once the system is up and running it should be audited to confirm that it meets the requirements of the standard and the expectations of the organisation.
The audits should include technical conformance checking in addition to process conformance. They should ideally be conducted by trained staff who are independent to the activity being audited but have sufficient knowledge to ensure that no wool is being pulled over they eyes! As usual, any weaknesses must be addressed in a controlled manner.
First Previous Next Last
Certification
The big question … should we go for external certification?
I feel that once an organisation has gone through the process of implementing an Information Security Management System it seems only right to get a third party in to assess the organisation to the ISO 27001 standard.
Achieving full compliance might not be appropriate for all organisations, but it is a powerful message to give to clients, shareholders and financial auditors. If you have used a consultant they should be able to assist you with this choice.
The benefits certainly outweigh the cost.
I have seen financial auditors visit an organisation on behalf of their clients to conduct an audit perhaps, as part of a SAS 70 or Sarbaines Oxley requirement or as part of a due diligence visit. It certainly lightens the air when one can reach for the certificate issued by an accredited independent third party!
When considering a certification body, the following should be on the list:
Make sure they are accredited by UKAS or other internationally recognised accreditation body
That the assessors have the right approach, knowledge and detailed experience in your industry
The size and profile of the certification body – in this global economy there are benefits in choosing one that’s present worldwide.
One that delivers practical advice and encourages continual development, as the standard requires.
First Previous Next Last
Sources of further information
The following is just a small sample of sites that provide additional information of information security and security advice:
http://www.sans.orghttp://www.mi5.gov.ukhttp://www.pwcglobal.com (use search box [security])http://www.niscc.gov.uk
ISO/IEC 27001 : 2005
Indian Standard
INFORMATION TECHNOLOGY SECURITY TECHNIQUES - INFORMATION SECURITY MANAGEMENT SYSTEMS - REQUIREMENTS
IMPORTANT - This publication does not purport to include all the necessary provisions of a contract. Users are responsible for its correct application. Compliance with an International Standard does not in itself confer immunity from legal obligations.
1 Scope
1.1 General
This International Standard covers all types of organizations (e.g. commercial enterprises, government agencies, non-profit organizations). This International Standard specifies the requirements for establishing, implementing, operating, monitoring, reviewing, maintaining and improving a documented ISMS within the context of the organization's overall business risks. It specifies requirements for the implementation of security controls customized to the needs of individual organizations or parts thereof.
The ISMS is designed to ensure the selection of adequate and proportionate security controls that protect information assets and give confidence to interested parties.
NOTE 1: References to 'business' in this Intemational Standard should be interpreted broadly to mean those activities that are core to the purposes for the organization's existence. .
NOTE 2: ISOllEe 17799 provides implementation guidance that can be used when designing controls.
1.2 Application
The requirements set out in this International Standard are generic and are intended to be applicable to all organizations, regardless of type, size and nature. Excluding any of the requirements specified in Clauses 4, 5,6,7, a'nd 8 is not acceptable when an organization claims conformity to this International Standard.
Any exclusion of controls found to be necessary to satisfy the risk acceptance criteria needs to be justified and evidence needs to be provided that the associated risks have been accepted by accountable persons. Where any controls are excluded, claims of conformity to this International Standard are not acceptable unless such exclusions do not affect the organization's ability, and/or responsibility, to provide information security that meets the security requirements determined by risk assessment and applicable legal or regulatory " requirements. .
NOTE: If an organization already has an operative business process management system (e.g. in relation with ISO 9001 or ISO 14001), it is preferable in most cases to satisfy the requirements of this International. Standard within this existing management system. '
The following referenced documents are indispensable for the application of this document. For dated references, only the edition cited applies. For undated references, the latest edition of the referenced document (including any amendments) applies.
ISO/IEC 17799:2005, Information technology - Security techniques -' Code of practice for information security management
4.2 Establishing and managing the ISMS
4.2.1 Establish the ISMS
The organization shall do the following.
a) Define the scope and boundaries of the ISMS in terms of the characteristics of the business, the organization, its location, assets and technology, and including details of and justification for any exclusions from the scope (see 1.2).
b) Define an ISMS policy in terms of the characteristics of the business, the organization, its location, assets and technology that:
1) includes a framework for setting objectives and establishes an overall sense of direction and principles for action with regard to information security;
2) takes into account business and legal or regulatory requirements, and contractual security obligations;
3) aligns with the organization's strategic risk management context in which the establishment and maintenance of the ISMS will take place;
4) establishes criteria against which risk will be evaluated (see 4.2.1 c»; and
5) has been approved by management.
NOTE: For the purposes of this International Standard, the ISMS policy is considered as a superset of the infornation security policy. These policies can be described in one document.
c) Define the risk assessment approach of the organization.
1) Identify a risk assessment methodology that is suited to the ISMS, and the identified business information security, legal and regulatory requirements.
2) Develop criteria for accepting risks and identify the acceptable levels of risk.· (see 5.1f».
The risk assessment methodology selected shall ensure that risk assessments produce comparable and ~eproducible results.
NOTE: There are different methodologies for risk assessment. Examples of risk assessment methodologies are discussed in ISO/IEC TR 13335-3, Information technology- Guidelines for the management of IT SecurityTechniques for the management of IT Security.
d) Identify the risks.
1) Identify the assets within the scope of the ISMS, and the owners2) of these assets.
2) Identify the threats to those assets.
3) Identify the vulnerabilities that might be exploited by the threats.
4) Identify the impacts that losses of confidentiality, integrity and availability may have on the assets.
2) The tenn 'owner' identifies an individual or entity that has. approved management responsibifrty for controlling the production, development, maintenance, use and security of the assets. The tenn 'owner' does not mean that the person actually has any property rights to the asset.
e) Analyse and evaluate the risks.
1) Assess the business impacts upon the organization that might result from security failures, taking i.nto account the consequences of a loss of confidentiality, integrity or availability of the assets.
2) Assess the realistic tikelihood of security failures occurring in the lightof prevailing threats and vulnerabilities, and impacts associated with these assets, and the controls currently implemented.
3) Estimate the levels of risks.
. 4) Determir.e whether the risks are acceptable Qr,requiretreatmentusing the criteria for (3cceptingrisks established in 4.2.1c)2).
f) Identify and evaluate options for the treatment of risks.
Possible actions include:
t) applying appropriate controls;
2) knowingly and objectively accepting risks, providing they clearly satisfy the organization's policies and the criteria for accepting risks (see 4.2.1c)2»;
3) avoiding risks; and
4) transferring the associated business risks to other parties. e.g. insurers, suppliers.
g) Select control objectives and controls for the treatment of risks.
Control objectives and controls shall be selected and implemented to meet the requirements identified by the risk assessment and risk treatment process. This selection shall take account of the criteria for accepting risks (see 4.2.1c)2» as well as legal, regulatory and contractual requirements.
The control objectives and controls from Annex A shall be selected as part of this process as suitable to cover the identified requirements.
The control objectives and controls listed in Annex A are not exhaustive and additional control objectives and controls may also be selected.
,
NOTE: Annex A contains a comprehensive list of control objectives and controls that have been found to be commonly relevant in organizations. Users of this Intemational Standard are directed to Annex A as a starting point for control selection to ensure that no important control options are overlooKe.d.
h) Obtajn management approval of the proposed residualrisks.
i) Obtain management authorization to implement and operate the ISMS.
j) Prepare a Statement of Applicability.
A Statement of Applicability shall be prepared that includes the following:
1) the control objectives and controls selected in 4.2.1 g) and the reasons for their selection;
2) thecontrol objectives and controls currently implemented (see 4.2.1e)2»;and
3) the exclusion of any control objectives and controls in Annex A and the justification for their exclusion.
NOTE: The Statement of Applicability provides a summary of decisions concerning risk treatment. Justifying exclusions provides a cross-check that no controls have been inadvertently omitted.
4.2.2 Implement and operate the ISMS
The organization shall do the following.
a) Formulate a risk treatnent plan that identifies the appropriate management action, resources, responsibilities arid priorities for managing information security risks (see 5).
b) Implement the risk treatment plan in order to achieve the identified control objectives, which includes consideration of funding and allocation of roles and responsibilities.
c) Implement controls selected in 4.2.1g) to meet the control objectives.
d) Define how to measure the effectiveness of the selected controls or groups of controls and specify how these measurements are to be used to assess control effectiveness to produce comparable and reproducible results (see 4.2.3c».
'.
NOTE: Measuring the effectiveness of controls allows managers and staff to determine how well controls achieve planned control objectives.
e) Implement training and awareness programmes (see 5.2.2).
f) Manage operation of the ISMS.
g) Manage resources for the ISMS (see 5.2).
h} !mplement procedures and other controls capable of enabling prompt detection of security events and response to security incidents (see 4.2.3a».
4.2.3 Monitor and review the ISMS
The organization shall do the following.
a) Execute monitoring and reviewing procedures and other controls to:
1) promptly detect errors in the results of processing;
2) promptly identify attempted and successful security breaches and incidents;
,
3} enable management to determine whether the security activities delegated to people or implemented by information technology are performing as expected;
4) help detect security events and thereby prevent security incidents by the use of indicators; and
5) determine whether the actions taken to resolve a breach of security were effective.
b) Undertake regular reviews of the effectiveness of the ISMS (including meeting ISMS policy and objectives, and review'of security controls) taking into account results of security audits, incidents, results from effectiveness measurements, suggestions and feedback from all interested parties.
c) Measure the effectiveness of controls to verify that security requirements have been met.
d) Review risk assessments at planned intervals and review the residual risks and the identified acceptable levels of risks, taking into account changes to:
1) the organization;
2) technology;
3) business objectives and processes;
4) identified threats;
5) effectiveness of the implemented controls; and
6) external events, such as changes to the legal or regulatory environment, changed contractual obligations, and changes in social climate.
Conduct internal ISMS audits at planned intervals (see 6).
NOTE: Internal audits, sometimes called first party audits, are conducted by, or on behalf of, the organization itself for internal purposes.
Undertake a management review of the ISMS on a regular basis to ensure that the scope remains adequate and improvements in the ISMS process are identified (see 7.1).
Update security plans to take into account the findings of monitoring and reviewing activities.
Record actions and events that could have an impact on the effectiveness or performance of the ISMS (see 4.3.3).
4.2.4 Maintain and improve the ISMS
1e organization shall regularly do the following.
, Implement the identified improvements in the ISMS.
I Take appropriate corrective and preventive actions in accordance with 8.2 and 8.3. Apply the lessons learnt from the security experiences of other organizations and those of the organization itself.
I Communicate the actions and improvements to all interested parties with a level of detail appropriate to the circumstances and, as relevant, agree on how to proceed.
Ensure that the improvements achieve their intended objectives_
4.2.3 Documentation requirements
4.2.3.1 General
documentation shall include records of management decisions, ensure that actions are traceable to lanagement decisions and policies, and ensure that the recorded results are reproducible.
it is important to be able to demonstrate the relationship from the selected controls back to the results of the Isk assessment and risk treatment process, and subsequently back to the ISMS policy and objectives.
"he ISMS documentation shall include:
I) documented statements of the ISMS policy (see 4.2.1b» and objectives;
I) the scope of the ISMS (see4.2.1a»;
:) procedures and controls in support of the ISMS;
j) a description of fhe risk assessment methodology (see 4.2.1c»;
~) the risk assessment report (see 4.2.1 c) to 4.2.1 g»;
) the risk treatment plan (see4.2..2b»;
1. Overview2. Introduction to Implementing an ISMS3. The OECD Guidelines4. Getting started5. Planning for success6. Understanding the standard
7. Where next...?8. Management processes9. Define the scope10. ISMS policy11. Risk assessment and management12. Risk treatment13. Certification
Implementing an Information Security Management System (ISMS) — LRQA Guidance
Why is BS7799 (ISO 17799) good for you?
Whether you manage internal information management systems, are responsible for information security or develop IT products and services for your customers, effective information security management systems (ISMS) are essential. They will help ensure you develop the right controls, systems and products to meet the ever increasing and demanding requirements of your customers and partners.
BS7799 aims to ensure that adequate controls (addressing confidentiality, integrity and availability of information) are in place to safeguard the information of ‘interested parties’. These include your customers, employees, trading partners and the needs of society in general.
An ISMS compliant to BS7799 part 2 can help you demonstrate to trading partners and customers alike that you take information security seriously. Accredited certification to BS 7799 is a powerful demonstration of an organisation’s commitment in managing information security.
This article provides some practical guidance and advice for those who have been tasked in gaining certification for their organisations with regards ISMS. A complementary document: ‘Implementing an ISMS - a Consultant’s Viewpoint’ is currently in preparation.
This article has been written by Geoff Brooks, LRQA Technical Services Manager
more
Implementing an ISMS — Consultants Viewpoint
1. Overview2. Benefits3. The initial steps4. Selecting a consultant5. Scoping the system6. Deriving the list of assets
7. Risk assessment8. Statement of applicability (SoA)9. Audit the system10. Certification11. Sources of further information
Implementing an Information Security Management System (ISMS) — Consultants Viewpoint
Is ISO 27001 right for your organisation?
In today's information society, electronic data is critical for almost everything we do. We rely on Internet connectivity and email. Laptops and PDA's have enabled a new mobile workforce. In short, information has now become a truly business critical asset. Protecting this asset through developing robust information security strategies and implementing effective information security controls is a key management responsibility.
Additionally, on account of the ever-increasing amount of legislation relating to the processing and storage of information, managers have a statutory responsibility to ensure that their company's data is protected.
Most companies will have implemented an information security management system to one degree or another. Achieving full compliance with a recognised industry standard is a way of demonstrating to clients, both existing and potential, as well as to shareholders, that your company is serious about information security governance.
ISO 27001 is the international standard for information security management and provides the ideal benchmark for certification. The benefits of embedding this standard in your information security management system (ISMS) should become apparent in the very early stages of implementation - and deliver lasting value to your organisation.
The purpose of this article is to help managers decide if a formal ISMS is appropriate for their organisation. It is written by Malcolm Armitage, a registered CISSP (Certified Information Systems Security Professional) with (ISC)².
Malcolm is a Director with SeQuality Management Solutions Ltd (www.sequality.co.uk) with many years experience helping organisations develop and implement such systems and achieve ISO 27001 certification. It is written from the consultant perspective and is designed to be read in conjunction with the LRQA Guidance article.
This article has been written by Malcolm Armitage, Independent Consultant.
First Previous Next Last
Benefits
Clients have cited several benefits associated with implementing a formal ISMS and achieving certification:
Increases potential client base and sales pipeline through satisfying specific contractual demands
Protects the value of IT investments
Reduces reputational risk
Integrates disaster recovery / business continuity
Formalises the asset inventory
Avoids security incidents lying dormant and dropping off the radar
Embeds continuous improvement in information security processes
Assists external financial auditors and simplifies the audit process
First Previous Next Last
The initial steps
Let us look first at what we are trying to achieve by implementing an ISMS. In this day and age we rely more and more on information in electronic form (although paper documents must not be precluded from this). You should stand back and imagine how your organisation would (or could) cope if this key information was lost or corrupted, or its confidentiality was compromised.
A small company who may use a computer for payroll and a few letters would probably be not significantly disrupted if all were lost. Providing the payroll could be manually re-created and not too many key addresses were lost, business could continue as usual.
However, if a larger organisation suffered a similar incident just one of the following could be disastrous:
If the information became unavailable – imagine trying to access files or databases and they weren’t there and could not be reconstructed; or
if the confidentiality of the data was compromised and key addresses and personal information was available to unauthorised persons; or
if the data became corrupted – such as account details or the contact database.
An organisation could go out of business overnight if adequate steps had not been taken. So this is the starting point: – deciding if an ISMS is necessary. A full business case containing both financial and qualitative benefits should be developed.
With ISO 27001 the organisation has the option to ‘ring fence’ different activities. As an example, an organisation may decide to apply certain controls to specific contracts or certain processes.
It is essential to get top-level management buy-in, not just to authorise the expenditure but to covey to the organisation that information security is taken very seriously and that if policies aren’t adhered to, disciplinary action may be taken. A full business case containing both financial and qualitative benefits should be developed and this can help get senior management buy-in.
Once again, the initiative will fail without a high degree of management commitment.
A project team should be established with members from key departments – this should be a business initiative and not purely reliant on the IT department. This is to ensure that all relevant and applicable information is captured from around the organisation.
First Previous Next Last
Selecting a consultant
You may decide not to involve a consultant and go it alone, after all information security isn’t rocket science, just good business practice. You may choose a combination of both internal and external resource. However, it is important to factor in the cost of these internal resources into the business case.
Whichever way you look at it, there is a cost involved whether it’s fees paid to an external consultant or hours charged to the project by using internal resource. Don’t forget that the external consultants will have done this before and should be able to reduce the duration of the project.
When it comes to selecting an external consultant a referral must be the preferred option. One who comes highly recommended from a colleague or business associate knows that you are aware of his approach and method of working.
If a referral is not possible, consider contacting your local Business Link, (http://www.businesslink.gov.uk/) who have access to a national register of approved consultants. The assessment is independent and reviewed annually. The British Computer Society (www.bcs.org) also maintains a register of consultants known as The Professional Advice Register.
Another option is to approach the assessment companies. These often have a list of consultants that their clients have used. They may be able to supply a list of two or three people for you to consider.
There are many factors to consider when choosing a consultant which include:
Do they have recognised skills and qualifications which can be verified? There are several schemes that require consultants to take exams to demonstrate a level of competence and in some cases require CPD credits e.g.
(ISC)² - International Information Systems Security Certification Consortium administers the examinations for the Certified Information Systems Security Professional (CISSP). They provide a portal where a consultant’s qualification can be verified. http://www.isc2.org/
BCS – British Computer Society administers the ISEB (Information Systems Examinations Board) CiISMP exam. http://www.bcs.org/
Can they provide client references of successful implementations/certifications? It is important that you understand the past experience of the specific consultants that will be working on your project rather than simply the consulting company they work for. Most companies will be able to provide a page of logos – try to ascertain what was really achieved.
Do they demonstrate an understanding of your business and specific requirements? Consultants should recognise that every business is different and not simply attempt to roll out what they have done on previous projects. Their approach and experience should be tailored to your needs, rather than them tailoring your needs to their experience and methodologies.
If all the above factors are met, you should ask yourself the most important question: Do I like these guys? You don’t have to invite them to your house for dinner, but for the implementation to be successful you will have to develop a deep working relationship. Remember that, from your perspective, consultancy companies are only as good as the resources they put on the ground.
First Previous Next Last
Scoping the system
Consider carefully what the ISMS is intended to cover and what you expect to get from it. It’s important to include all the activities that fall within the scope of the ISMS. Should you seek formal certification, this is what your assessment body will use as the starting point.
Potential customers may well ask to see the approved scope to ensure you can provide, and are assessed to provide, exactly what they require.
The objectives should also be considered and documented. Think carefully about these. The days of ‘we want to be best in class’ have gone. The standards now require that an element of continual improvement is demonstrable.
Identify and engage key stakeholders and assemble the correct project team. Implementing an ISMS involves more than just the IT organisation and it is important that the business as a whole sees the benefits of the implementation and understands its impact. Team size and the appropriate project leader are specific to each organisation. The project team should be able to devote sufficient time to the implementation. A smaller group of closely involved individuals is usually more effective than a larger team of occasional part-timers. Should you have engaged a consultant, it is important that they are supported by internal resources: nobody understands the business better than those working in it. When consultants leave, knowledge can walk out the door with them.
As with any new project, a plan should be produced, but be realistic. If funding is sought from your local Business Link, they may require sight of the plan. The complexity of this will depend on the size of the organisation and the scope of the ISMS. You may decide that the ISMS is to be applied to only some activities within the organisation.
Try to keep your plan relatively simple yet include sufficient detail to show important milestones. Include review activities on the plan so that progress can be formally monitored. Update the plan on a regular basis. Ensure you keep senior management informed of progress.
First Previous Next Last
Deriving the list of assets
It’s important to establish just what needs protection. It may sound obvious, but the first part of understanding what you need to protect is understanding what you have. This is not always immediately apparent as it is important to value each asset not just in terms of financial value but also in terms of the impact such a loss would have on the organisation. In order to do this you should nominate representatives from each department or key areas. When building this list it’s important to capture all the obvious and important assets such as the electronic ones, but don’t forget the old analogue modem that’s used daily by accounts to pay people etc. Conversely, make sure that the not so important assets in the organisation are excluded.
Remember that you are trying to capture the key components that need consideration in terms of information security. Consider the ‘what if’ scenario on the selected asset: what would it mean in terms of financial loss or reputation if they became unavailable or corrupted (the business impact analysis). Also take into consideration the fact that company assets may be located offsite – laptops are an example of this.
First Previous Next Last
Risk assessment
Once the list of assets has been established a risk assessment methodology should be selected and undertaken on these assets. There are tools available to assist with the risk assessment process that may be worth considering. Which ever risk assessment methodology is selected it’s important that it is appropriate and repeatable.
A risk treatment plan should be produced to manage and mitigate the identified risks. Appropriate controls can then be selected from ISO 27001 Annex A to satisfy the risk assessment and risk treatment requirements.
First Previous Next Last
Statement of applicability (SoA)
An SoA must be prepared that shows the controls that have been selected from ISO 27001 and the reasons for their selection. It must also show the controls currently implemented. Where any controls have not been selected because they are inappropriate for the organisation, the justification for their exclusion must also be noted.
First Previous Next Last
Audit the system
As with other management systems once the system is up and running it should be audited to confirm that it meets the requirements of the standard and the expectations of the organisation.
The audits should include technical conformance checking in addition to process conformance. They should ideally be conducted by trained staff who are independent to the activity being audited but have sufficient knowledge to ensure that no wool is being pulled over they eyes! As usual, any weaknesses must be addressed in a controlled manner.
First Previous Next Last
Certification
The big question … should we go for external certification?
I feel that once an organisation has gone through the process of implementing an Information Security Management System it seems only right to get a third party in to assess the organisation to the ISO 27001 standard.
Achieving full compliance might not be appropriate for all organisations, but it is a powerful message to give to clients, shareholders and financial auditors. If you have used a consultant they should be able to assist you with this choice.
The benefits certainly outweigh the cost.
I have seen financial auditors visit an organisation on behalf of their clients to conduct an audit perhaps, as part of a SAS 70 or Sarbaines Oxley requirement or as part of a due diligence visit. It certainly lightens the air when one can reach for the certificate issued by an accredited independent third party!
When considering a certification body, the following should be on the list:
Make sure they are accredited by UKAS or other internationally recognised accreditation body
That the assessors have the right approach, knowledge and detailed experience in your industry
The size and profile of the certification body – in this global economy there are benefits in choosing one that’s present worldwide.
One that delivers practical advice and encourages continual development, as the standard requires.
First Previous Next Last
Sources of further information
The following is just a small sample of sites that provide additional information of information security and security advice:
http://www.sans.orghttp://www.mi5.gov.ukhttp://www.pwcglobal.com (use search box [security])http://www.niscc.gov.uk
ISO/IEC 27001 : 2005
Indian Standard
INFORMATION TECHNOLOGY SECURITY TECHNIQUES - INFORMATION SECURITY MANAGEMENT SYSTEMS - REQUIREMENTS
IMPORTANT - This publication does not purport to include all the necessary provisions of a contract. Users are responsible for its correct application. Compliance with an International Standard does not in itself confer immunity from legal obligations.
1 Scope
1.1 General
This International Standard covers all types of organizations (e.g. commercial enterprises, government agencies, non-profit organizations). This International Standard specifies the requirements for establishing, implementing, operating, monitoring, reviewing, maintaining and improving a documented ISMS within the context of the organization's overall business risks. It specifies requirements for the implementation of security controls customized to the needs of individual organizations or parts thereof.
The ISMS is designed to ensure the selection of adequate and proportionate security controls that protect information assets and give confidence to interested parties.
NOTE 1: References to 'business' in this Intemational Standard should be interpreted broadly to mean those activities that are core to the purposes for the organization's existence. .
NOTE 2: ISOllEe 17799 provides implementation guidance that can be used when designing controls.
1.2 Application
The requirements set out in this International Standard are generic and are intended to be applicable to all organizations, regardless of type, size and nature. Excluding any of the requirements specified in Clauses 4, 5,6,7, a'nd 8 is not acceptable when an organization claims conformity to this International Standard.
Any exclusion of controls found to be necessary to satisfy the risk acceptance criteria needs to be justified and evidence needs to be provided that the associated risks have been accepted by accountable persons. Where any controls are excluded, claims of conformity to this International Standard are not acceptable unless such exclusions do not affect the organization's ability, and/or responsibility, to provide information security that meets the security requirements determined by risk assessment and applicable legal or regulatory " requirements. .
NOTE: If an organization already has an operative business process management system (e.g. in relation with ISO 9001 or ISO 14001), it is preferable in most cases to satisfy the requirements of this International. Standard within this existing management system. '
The following referenced documents are indispensable for the application of this document. For dated references, only the edition cited applies. For undated references, the latest edition of the referenced document (including any amendments) applies.
ISO/IEC 17799:2005, Information technology - Security techniques -' Code of practice for information security management
4.2 Establishing and managing the ISMS
4.2.1 Establish the ISMS
The organization shall do the following.
a) Define the scope and boundaries of the ISMS in terms of the characteristics of the business, the organization, its location, assets and technology, and including details of and justification for any exclusions from the scope (see 1.2).
b) Define an ISMS policy in terms of the characteristics of the business, the organization, its location, assets and technology that:
1) includes a framework for setting objectives and establishes an overall sense of direction and principles for action with regard to information security;
2) takes into account business and legal or regulatory requirements, and contractual security obligations;
3) aligns with the organization's strategic risk management context in which the establishment and maintenance of the ISMS will take place;
4) establishes criteria against which risk will be evaluated (see 4.2.1 c»; and
5) has been approved by management.
NOTE: For the purposes of this International Standard, the ISMS policy is considered as a superset of the infornation security policy. These policies can be described in one document.
c) Define the risk assessment approach of the organization.
1) Identify a risk assessment methodology that is suited to the ISMS, and the identified business information security, legal and regulatory requirements.
2) Develop criteria for accepting risks and identify the acceptable levels of risk.· (see 5.1f».
The risk assessment methodology selected shall ensure that risk assessments produce comparable and ~eproducible results.
NOTE: There are different methodologies for risk assessment. Examples of risk assessment methodologies are discussed in ISO/IEC TR 13335-3, Information technology- Guidelines for the management of IT SecurityTechniques for the management of IT Security.
d) Identify the risks.
1) Identify the assets within the scope of the ISMS, and the owners2) of these assets.
2) Identify the threats to those assets.
3) Identify the vulnerabilities that might be exploited by the threats.
4) Identify the impacts that losses of confidentiality, integrity and availability may have on the assets.
2) The tenn 'owner' identifies an individual or entity that has. approved management responsibifrty for controlling the production, development, maintenance, use and security of the assets. The tenn 'owner' does not mean that the person actually has any property rights to the asset.
e) Analyse and evaluate the risks.
1) Assess the business impacts upon the organization that might result from security failures, taking i.nto account the consequences of a loss of confidentiality, integrity or availability of the assets.
2) Assess the realistic tikelihood of security failures occurring in the lightof prevailing threats and vulnerabilities, and impacts associated with these assets, and the controls currently implemented.
3) Estimate the levels of risks.
. 4) Determir.e whether the risks are acceptable Qr,requiretreatmentusing the criteria for (3cceptingrisks established in 4.2.1c)2).
f) Identify and evaluate options for the treatment of risks.
Possible actions include:
t) applying appropriate controls;
2) knowingly and objectively accepting risks, providing they clearly satisfy the organization's policies and the criteria for accepting risks (see 4.2.1c)2»;
3) avoiding risks; and
4) transferring the associated business risks to other parties. e.g. insurers, suppliers.
g) Select control objectives and controls for the treatment of risks.
Control objectives and controls shall be selected and implemented to meet the requirements identified by the risk assessment and risk treatment process. This selection shall take account of the criteria for accepting risks (see 4.2.1c)2» as well as legal, regulatory and contractual requirements.
The control objectives and controls from Annex A shall be selected as part of this process as suitable to cover the identified requirements.
The control objectives and controls listed in Annex A are not exhaustive and additional control objectives and controls may also be selected.
,
NOTE: Annex A contains a comprehensive list of control objectives and controls that have been found to be commonly relevant in organizations. Users of this Intemational Standard are directed to Annex A as a starting point for control selection to ensure that no important control options are overlooKe.d.
h) Obtajn management approval of the proposed residualrisks.
i) Obtain management authorization to implement and operate the ISMS.
j) Prepare a Statement of Applicability.
A Statement of Applicability shall be prepared that includes the following:
1) the control objectives and controls selected in 4.2.1 g) and the reasons for their selection;
2) thecontrol objectives and controls currently implemented (see 4.2.1e)2»;and
3) the exclusion of any control objectives and controls in Annex A and the justification for their exclusion.
NOTE: The Statement of Applicability provides a summary of decisions concerning risk treatment. Justifying exclusions provides a cross-check that no controls have been inadvertently omitted.
4.2.2 Implement and operate the ISMS
The organization shall do the following.
a) Formulate a risk treatnent plan that identifies the appropriate management action, resources, responsibilities arid priorities for managing information security risks (see 5).
b) Implement the risk treatment plan in order to achieve the identified control objectives, which includes consideration of funding and allocation of roles and responsibilities.
c) Implement controls selected in 4.2.1g) to meet the control objectives.
d) Define how to measure the effectiveness of the selected controls or groups of controls and specify how these measurements are to be used to assess control effectiveness to produce comparable and reproducible results (see 4.2.3c».
'.
NOTE: Measuring the effectiveness of controls allows managers and staff to determine how well controls achieve planned control objectives.
e) Implement training and awareness programmes (see 5.2.2).
f) Manage operation of the ISMS.
g) Manage resources for the ISMS (see 5.2).
h} !mplement procedures and other controls capable of enabling prompt detection of security events and response to security incidents (see 4.2.3a».
4.2.3 Monitor and review the ISMS
The organization shall do the following.
a) Execute monitoring and reviewing procedures and other controls to:
1) promptly detect errors in the results of processing;
2) promptly identify attempted and successful security breaches and incidents;
,
3} enable management to determine whether the security activities delegated to people or implemented by information technology are performing as expected;
4) help detect security events and thereby prevent security incidents by the use of indicators; and
5) determine whether the actions taken to resolve a breach of security were effective.
b) Undertake regular reviews of the effectiveness of the ISMS (including meeting ISMS policy and objectives, and review'of security controls) taking into account results of security audits, incidents, results from effectiveness measurements, suggestions and feedback from all interested parties.
c) Measure the effectiveness of controls to verify that security requirements have been met.
d) Review risk assessments at planned intervals and review the residual risks and the identified acceptable levels of risks, taking into account changes to:
1) the organization;
2) technology;
3) business objectives and processes;
4) identified threats;
5) effectiveness of the implemented controls; and
6) external events, such as changes to the legal or regulatory environment, changed contractual obligations, and changes in social climate.
Conduct internal ISMS audits at planned intervals (see 6).
NOTE: Internal audits, sometimes called first party audits, are conducted by, or on behalf of, the organization itself for internal purposes.
Undertake a management review of the ISMS on a regular basis to ensure that the scope remains adequate and improvements in the ISMS process are identified (see 7.1).
Update security plans to take into account the findings of monitoring and reviewing activities.
Record actions and events that could have an impact on the effectiveness or performance of the ISMS (see 4.3.3).
4.2.4 Maintain and improve the ISMS
1e organization shall regularly do the following.
, Implement the identified improvements in the ISMS.
I Take appropriate corrective and preventive actions in accordance with 8.2 and 8.3. Apply the lessons learnt from the security experiences of other organizations and those of the organization itself.
I Communicate the actions and improvements to all interested parties with a level of detail appropriate to the circumstances and, as relevant, agree on how to proceed.
Ensure that the improvements achieve their intended objectives_
4.2.3 Documentation requirements
4.2.3.1 General
documentation shall include records of management decisions, ensure that actions are traceable to lanagement decisions and policies, and ensure that the recorded results are reproducible.
it is important to be able to demonstrate the relationship from the selected controls back to the results of the Isk assessment and risk treatment process, and subsequently back to the ISMS policy and objectives.
"he ISMS documentation shall include:
I) documented statements of the ISMS policy (see 4.2.1b» and objectives;
I) the scope of the ISMS (see4.2.1a»;
:) procedures and controls in support of the ISMS;
j) a description of fhe risk assessment methodology (see 4.2.1c»;
~) the risk assessment report (see 4.2.1 c) to 4.2.1 g»;
) the risk treatment plan (see4.2..2b»;
Subscribe to:
Post Comments (Atom)















.jpg)





.jpg)

.jpg)









.jpg)

.jpg)














.jpg)


.jpg)


























































































































































































































.jpg)

.jpg)











.jpg)




















































.jpg)
















.jpg)












































































































































.jpg)

























No comments:
Post a Comment