Sunday, February 15, 2009
ISO 27001/2: Common Mistakes
ISO 27001/2: Common Mistakes Part 3
===================================
David Watson was one of the first exponents of the standards, and is
one of the most well known industry figures. In the third of this
series of articles for the ISO 27000 Newsletter he outlines some of
the most common errors and mistakes he has encountered over the years:
Physical & Environmental Security
• Supposedly secure buildings can easily have their physical security
breached by a variety of means (e.g. social engineering, piggybacking,
fire doors left open etc.);
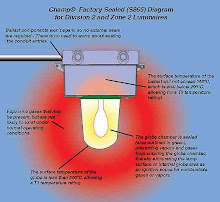
• Power supplies are often unprotected against unauthorized access.
• Critical equipment is not always protected by UPS;
• Generators and UPS are often not regularly tested, or the test
results are not available;
• Equipment maintenance is not always carried out in accordance with
manufacturers instructions – possibly invalidating the manufacturers
warranty;
• Off premises security of equipment is often overlooked by the
organization;
• Secure disposal / removal of equipment is often not recorded or
carried out securely, potentially leading to unauthorized disclosure
of information;
• Clear desk / screen processes are often not carried out, especially
in the IT Department. Usually, but not always, IT forces other users
to have clear screens, but often there is no clear desk process in
place and no lockable cabinets to store securely anything needed to be
locked away due to its classification. This can be exacerbated if
there is no information classification process in place and used
across the organization or if there are no handling procedures based
on the information classifications.
Asset Classification and Control
• There is often little or no concept of data or information
ownership, or of asset classification;
• There is often little control over movement of equipment;
• Security (if implemented) is not based on this process (or
associated risk management processes);
• There is sometimes little, if any, personal accountability by
anyone, especially owners (whether they are aware of their role or
not);
• Owners rarely review their information from a security viewpoint;
• Information (of any sort) is rarely classified consistently and
handled according to the requirements of that classification
Protecting Against Malicious Code Attacks
more
===================================
David Watson was one of the first exponents of the standards, and is
one of the most well known industry figures. In the third of this
series of articles for the ISO 27000 Newsletter he outlines some of
the most common errors and mistakes he has encountered over the years:
Physical & Environmental Security
• Supposedly secure buildings can easily have their physical security
breached by a variety of means (e.g. social engineering, piggybacking,
fire doors left open etc.);
• Power supplies are often unprotected against unauthorized access.
• Critical equipment is not always protected by UPS;
• Generators and UPS are often not regularly tested, or the test
results are not available;
• Equipment maintenance is not always carried out in accordance with
manufacturers instructions – possibly invalidating the manufacturers
warranty;
• Off premises security of equipment is often overlooked by the
organization;
• Secure disposal / removal of equipment is often not recorded or
carried out securely, potentially leading to unauthorized disclosure
of information;
• Clear desk / screen processes are often not carried out, especially
in the IT Department. Usually, but not always, IT forces other users
to have clear screens, but often there is no clear desk process in
place and no lockable cabinets to store securely anything needed to be
locked away due to its classification. This can be exacerbated if
there is no information classification process in place and used
across the organization or if there are no handling procedures based
on the information classifications.
Asset Classification and Control
• There is often little or no concept of data or information
ownership, or of asset classification;
• There is often little control over movement of equipment;
• Security (if implemented) is not based on this process (or
associated risk management processes);
• There is sometimes little, if any, personal accountability by
anyone, especially owners (whether they are aware of their role or
not);
• Owners rarely review their information from a security viewpoint;
• Information (of any sort) is rarely classified consistently and
handled according to the requirements of that classification
Protecting Against Malicious Code Attacks
more
Subscribe to:
Post Comments (Atom)















.jpg)





.jpg)

.jpg)









.jpg)

.jpg)














.jpg)


.jpg)


























































































































































































































.jpg)

.jpg)











.jpg)




















































.jpg)
















.jpg)












































































































































.jpg)

























No comments:
Post a Comment